为ASA配置ipsec vpn
实现配置步骤设备初始化
配置路由
配置NAT
配置ISAKMP/IKE阶段1
配置ISAKMP/IKE阶段2
测试
1、设备初始化ciscoasa(config)#hostname?ASAASA(config)#int?e0/0
ASA(config-if)#nameif?outsideASA(config-if)#security-level?0
ASA(config-if)#ip?add?172.16.2.1?255.255.255.0
ASA(config-if)#no?shASA(config)#int?e0/1
ASA(config-if)#nameif?inside
ASA(config-if)#security-level?100
ASA(config-if)#ip?add?192.168.20.254?255.255.255.0
ASA(config-if)#no?sh
VPN(config)#hostname?VPN
VPN(config)#int?e0/0
VPN(config-if)#ip?add?172.16.1.1?255.255.255.0
VPN(config-if)#no?sh
VPN(config)#int?e0/1
VPN(config-if)#ip?add?192.168.10.254?255.255.255.0
VPN(config-if)#no?sh
internet(config)#int?e0/0
internet(config-if)#ip?add?172.16.1.254?255.255.255.0
internet(config-if)#no?sh
internet(config)#int?e0/1
internet(config-if)#ip?add?172.16.2.254?255.255.255.0
internet(config-if)#no?sh
2、配置路由(保证VPN加/解密点之间能通信)ASA(config)#route?outside?0.0.0.0?0.0.0.0?172.16.2.254
VPN(config)#ip?route?0.0.0.0?0.0.0.0?172.16.1.254
3、配置NATASA(config)#access-list?NONAT?permit?ip?192.168.20.0?255.255.255.0?192.168.10.0?255.255.255.0---(不进行NAT转换)
ASA(config)#nat?(inside)?0?access-list?NONAT------表示NAT豁免技术ASA(config)#nat?(inside)?1?192.168.20.0?255.255.255.0
ASA(config)#global?(outside)?1?interfaceVPN(config)#ip?access-list?extended?NAT????定义什么流量进行NAT转
VPN(config-ext-nacl)#deny?ip?192.168.10.0?0.0.0.255?192.168.20.0?0.0.0.255------这是VPN的流量,所以不进行NAT转换
VPN(config-ext-nacl)#permit?ip?any?any?????允许其他流量进行NAT转换VPN(config)#ip?nat?inside?source?list?NAT?interface?e0/0?overload
VPN(config)#int?e0/0
VPN(config-if)#ip?nat?outside
VPN(config)#int?e0/1
VPN(config-if)#ip?nat?inside
4、配置ISAKMP/IKE阶段11)配置ISAKMP/IKE策略
ASA(config)#crypto?isakmp?enable?outside????启用ISAKMP协议ASA(config)#crypto?isakmp?policy?1?????定义第一阶段ISAKMP/IKE策略
ASA配置ipsecvpn_ISAKMP
ASA(config-isakmp)#hash?md5?????????哈希使用md5
ASA(config-isakmp)#encryption?des????加密方式使用Data?Encryption?Standard?(56?bit?keys).)
ASA(config-isakmp)#group?2?????????????DH加密算法强度
ASA(config-isakmp)#authentication?pre-share???验证用预共享密钥VPN(config)#crypto?isakmp?policy?1????定义第一阶段ISAKMP/IKE策略
VPN(config-isakmp)#hash?md5??????????哈希算法使用md5
VPN(config-isakmp)#encryption?des????加密方式使用Data?Encryption?Standard?(56?bit?keys).
VPN(config-isakmp)#group?2??????????????DH加密算强度
VPN(config-isakmp)#authentication?pre-share???验证用预共享密钥2)配置预共享密钥ASA(config)#crypto?isakmp?key??cisco?address?172.16.1.1
VPN(config)#crypto?isakmp?key??0?cisco?address?172.16.2.1
5、配置ISAKMP/IKE阶段21)、配置ACL定义VPN连接所保护的流量
ASA(config)#access-list?VPN?permit?ip?192.168.20.0?255.255.255.0?192.168.10.0?255.255.255.0
VPN(config)#ip?access-list?extended?VPN????定义vpn感兴趣流
VPN(config-ext-nacl)#permit?ip?192.168.10.0?0.0.0.255?192.168.20.0?0.0.0.255
2)、定义Ipsec传输集(转换集)
ASA(config)#crypto?ipsec?transform-set?ESP-T?esp-des?esp-md5-hmac
VPN(config)#crypto?ipsec?transform-set?ESP-T?esp-des?esp-md5-hmac
3)、配置crypto?map加密映射(作用:关联ACL和ipsec传输集设置)
ASA(config)#crypto?map?VPN-MAP?1?ipsec-isakmp?????全局启用ipsec-ISAKMP协议ASA(config)#crypto?map?VPN-MAP?1?match?address?VPN
ASA(config)#crypto?map?VPN-MAP?1?set?peer?172.16.1.1????指定对方的加/解点ASA(config)#crypto?map?VPN-MAP?1?set?transform-set?ESP-T
VPN(config)#crypto?map?VPN-MAP?1?ipsec-isakmp?????默认已开启
VPN(config-crypto-map)#set?transform-set?ESP-T??调用转换集
VPN(config-crypto-map)#match?address?VPN??????匹配需加密的流量
VPN(config-crypto-map)#set?peer?172.16.2.1?????指明对方加(解)密点
4)、crypto?map接口应用
ASA(config)#crypto?map?VPN-MAP?interface?outside
VPN(config)#int?e0/0
VPN(config-if)#crypto?map?VPN-MAP????端口调用加密映射
6、测试1)路由器VPN查看与排错命令:
Show?crypto?isakmp?policy ? ?显示所有尝试的策略以及最后的默认策略设置:clear?cry?session ?清除VPN连接
Show?crypto?ipsec?transform-set ?显示ipsec传输集设置
Show?crypto?map ? ?显示crypto?map相关配置
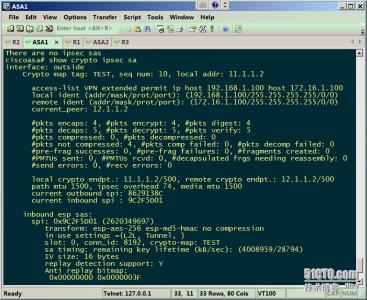
Show?cyrpto?isakmp?sa ? 显示ISAKMP/IKE阶段1安全联盟SA---VPN连接
Show?crypto?ipsec?sa ? ? 显示ISAKMP/IKE阶段2安全联盟SA
Show?crypto?engine?connction?active ? 显示VPN连接加解密的数据包数量
2)ASA防火墙VPN查看与排错命令:
ASA配置ipsecvpn_ISAKMP
show?vpn-sessiondb?l2l???查看l2l?vpn的连接状态信息
 爱华网
爱华网