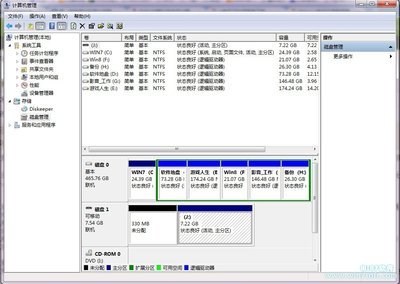
1、增加系统分区的分区格式判断,比如是NTFS分区还是FAT32分区;
2、增加streams.exe的EULA许可注册表文件导入,解决脚本不能正常运行的问题;
3、修改了显示所有文件夹函数的实现,改为vbs实现;
【注】请参考原文:http://hi.baidu.com/msrighthomepage/blog/item/ec0a053c01ee84e23c6d971c.html
本工具需要用到:boyfine专杀,还有streams.exe。下载地址:
快捷方式vbs病毒(“暴风一号”)专杀下载地址:http://www.onlinedown.net/soft/94530.htm
streams.exe下载地址:http://download.sysinternals.com/Files/Streams.zip
注意事项:把streams.exe放在这个脚本的目录下,先运行病毒专杀,然后再执行杀毒工具。
注意:把以下代码复制到“记事本”后,在“另存为”操作时,名称为“del.vbs”,“保存类型”为“所有文件”,“编码”为“ANSI”。
不然会提示错误信息,型如
行 :1字符:1错误:无效字符代码:800A0408源 : microsoft vbscript 编译器错误
Function GetSystemDrive()
On Error Resume Next
Set Fso=CreateObject("Scripting.FileSystemObject")
GetSystemDrive=Left(Fso.GetSpecialFolder(0),2)
End Function
Function GetFileSystemType(Drive)
On Error Resume Next
Set Fso=CreateObject("Scripting.FileSystemObject")
Set d=FSO.GetDrive(Drive)
GetFileSystemType=d.FileSystem
End Function
Sub ShowF(fpath)
On Error Resume Next
Set Fso=CreateObject("Scripting.FileSystemObject")
Set Folder=Fso.GetFolder(fpath)
Set SubFolders=Folder.Subfolders
For Each SubFolder In SubFolders
SubFolder.Attributes=0
Next
End Sub
Sub WriteReg(strkey, Value, vtype)
On Error Resume Next
Set WsShell=CreateObject("WScript.Shell")
If vtype="" Then
WsShell.RegWrite strkey, Value
Else
WsShell.RegWrite strkey, Value, vtype
End If
Set WsShell=Nothing
End Sub
Sub CreateFile(code, pathf)
On Error Resume Next
Set Fso=CreateObject("Scripting.FileSystemObject")
If Fso.FileExists(pathf) Then
Set FileText=Fso.OpenTextFile(pathf, 2, False)
FileText.Write code
FileText.Close
Else
Set FileText=Fso.OpenTextFile(pathf, 2, True)
FileText.Write code
FileText.Close
End If
End Sub
Sub DelReg(strkey)
On Error Resume Next
Set WsShell=CreateObject("WScript.Shell")
Set Fso=CreateObject("Scripting.FileSystemObject")
strkey="Windows Registry Editor Version 5.00"&vbCrlf&vbCrlf&strkey
CreateFile strkey, "d:temp.reg"
WsShell.run "%systemroot%regedit.exe /s d:temp.reg",0,true
Fso.DeleteFile "d:temp.reg", True
End Sub
Function GetSerialNumber(Drv)
On Error Resume Next
Set Fso=CreateObject("Scripting.FileSystemObject")
Set d=Fso.GetDrive(Drv)
GetSerialNumber=d.SerialNumber
GetSerialNumber=Replace(GetSerialNumber,"-","")
End Function
On Error Resume Next
If GetFileSystemType(GetSystemDrive())="NTFS" Then
Value=1
Call WriteReg("HKEY_USERSS-1-5-21-1177238915-1450960922-1801674531-1003SoftwareSysinternalsStreamsEulaAccepted", Value, "REG_DWORD")
End If
ans=msgbox("欢迎使用“暴风一号”查杀工具~如果想继续修复系统请选择“是”~",VbYesNo+vbInformation,"MsRightHomepage 的“暴风一号”查杀工具 ~")
If ans=vbNo Then
msgbox "脚本将退出并且不做任何处理!",VbYesOnly+vbInformation,"MsRightHomepage 的“暴风一号”查杀工具 ~"
wscript.quit
end if
Value="%SystemRoot%system32notepad.exe %1"
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREClassestxtfileshellopencommand", Value, "REG_EXPAND_SZ")
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREClassesinifileshellopencommand", Value, "REG_EXPAND_SZ")
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREClassesinffileshellopencommand", Value, "REG_EXPAND_SZ")
Value=Chr(34)&"%1"&Chr(34)&" %*"
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREClassesbatfileshellopencommand", Value, "REG_EXPAND_SZ")
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREClassescmdfileshellopencommand", Value, "REG_EXPAND_SZ")
Value="%SystemRoot%winhlp32.exe %1"
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREClasseshlpfileshellopencommand", Value, "REG_EXPAND_SZ")
Value="regedit.exe "&Chr(34)&"%1"&Chr(34)
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREClassesregfileshellopencommand", Value, "REG_EXPAND_SZ")
Value="%SystemRoot%system32hh.exe %1"
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREClasseschm.fileshellopencommand", Value, "REG_EXPAND_SZ")
Set WsShell=CreateObject("WScript.Shell")
WsShell.run "%SystemRoot%system32regsvr32.exe /s "&"%SystemRoot%system32hhctrl.ocx",0,true
Value="%ProgramFiles%Internet Exploreriexplore.exe"
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREClassesApplicationsiexplore.exeshellopencommand", Value, "REG_EXPAND_SZ")
Value=chr(34)&"%ProgramFiles%Internet ExplorerIEXPLORE.EXE"&chr(34)
Call WriteReg("HKEY_CLASSES_ROOTCLSID{871C5380-42A0-1069-A2EA-08002B30309D}shellOpenHomePageCommand", Value, "REG_EXPAND_SZ")
Value=""
Call WriteReg("HKEY_CURRENT_USERSoftWareMicrosoftWindows NTCurrentVersionWindowsLoad", Value, "")
Value="%SystemRoot%explorer.exe"
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}shellopencommand", Value, "REG_EXPAND_SZ")
Value="HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorerNoDriveTypeAutoRun"
Call WriteReg(Value, 255, "REG_DWORD")
Value=2
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionExplorerAdvancedFolderHiddenNOHIDDENCheckedValue", Value, "REG_DWORD")
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionExplorerAdvancedFolderHiddenNOHIDDENDefaultValue", Value, "REG_DWORD")
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionExplorerAdvancedFolderHiddenSHOWALLDefaultValue", Value, "REG_DWORD")
Value=1
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionExplorerAdvancedFolderHiddenSHOWALLCheckedValue", Value, "REG_DWORD")
Value="[-HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}shellexplore]"
Call DelReg(Value)
Value="[-HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}shellfind]"
Call DelReg(Value)
Value="我的电脑"
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}",Value,"REG_SZ")
Value="@%SystemRoot%system32SHELL32.dll,-22913"
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}InfoTip",Value,"REG_EXPAND_SZ")
Value="@%SystemRoot%system32SHELL32.dll,-31751"
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}IntroText",Value,"REG_EXPAND_SZ")
Value="@%SystemRoot%system32SHELL32.dll,-9216"
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}LocalizedString",Value,"REG_EXPAND_SZ")
Value="%SystemRoot%Explorer.exe,0"
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}DefaultIcon",Value,"REG_EXPAND_SZ")
Value="%SystemRoot%system32SHELL32.dll"
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}InProcServer32",Value,"REG_EXPAND_SZ")
Value="Apartment"
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}InProcServer32ThreadingModel",Value,"REG_SZ")
Value="none"
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}shell",Value,"REG_SZ")
Value="@%windir%system32mycomput.dll,-400"
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}shellManage",Value,"REG_EXPAND_SZ")
Value=&h4000003c
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}shellManageSuppressionPolicy",Value,"REG_DWORD")
Value="%windir%system32mmc.exe /s %windir%system32compmgmt.msc"
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}shellManagecommand",Value,"REG_EXPAND_SZ")
Value=""
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}ShellFolder",Value,"REG_SZ")
Call WriteReg("HKEY_CLASSES_ROOTCLSID{20D04FE0-3AEA-1069-A2D8-08002B30309D}ShellFolderHideOnDesktopPerUser",Value,"REG_SZ")
Value=1
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindows NTSystemRestoreDisableSR",Value,"REG_DWORD")
Call WriteReg("HKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftWindows NTSystemRestoreDisableConfig",Value,"REG_DWORD")
Set Fso=CreateObject("Scripting.FileSystemObject")
For Each Drive In Fso.Drives
If Drive.IsReady and (Drive.DriveType=1 Or Drive.DriveType=2 Or Drive.DriveType=3) Then
ShowF(Drive.DriveLetter&":")
DiskVirusName=GetSerialNumber(Drive.DriveLetter)&".vbs"
Fso.DeleteFile Drive.DriveLetter&":"&DiskVirusName, True
Fso.DeleteFile Drive.DriveLetter&":"&"autorun.inf", True
Fso.DeleteFile Drive.DriveLetter&":"&"*.lnk", True
msgbox Drive.DriveLetter&"盘修复完毕!",vbInformation+vbYesOnly,"MsRightHomepage 的“暴风一号”查杀工具 ~"
End If
Next
If GetFileSystemType(GetSystemDrive())="NTFS" Then
Set Fso=CreateObject("Scripting.FileSystemObject")
Set WsShell=CreateObject("WScript.Shell")
workingdir=WScript.ScriptFullName
workingdir=StrReverse(fso.getfile(workingdir).shortpath)
count=InStr(workingdir,"")
workingdir=StrReverse(Right(workingdir,Len(workingdir)-count))
If Fso.FileExists(workingdir&"streams.exe")=False Then
msgbox "未发现streams.exe文件,流病毒将不能被删除!"&vbCrlf&vbCrlf&"请下载streams.exe: http://download.sysinternals.com/Files/Streams.zip"&vbCrlf&vbCrlf&"并且把streams.exe解压出来放在该脚本目录下~",vbCritical+vbYesOnly,"MsRightHomepage 的“暴风一号”查杀工具 ~"
Else
windir0=Fso.getspecialfolder(0)
cmdline=workingdir&"streams.exe -d "&windir0&"*"
WsShell.Run cmdline,vbHide,True
windir1=Fso.getspecialfolder(1)
cmdline=workingdir&"streams.exe -d "&windir1&"*"
WsShell.Run cmdline,vbHide,True
End If
Else
Set Fso=CreateObject("Scripting.FileSystemObject")
MainVirusName=GetSerialNumber(GetSystemDrive())&".vbs"
GetMainVirus=Fso.GetSpecialFolder(0)&""&MainVirusName
Fso.DeleteFile GetMainVirus
GetMainVirus=Fso.GetSpecialFolder(1)&""&MainVirusName
Fso.DeleteFile GetMainVirus
End If
Fso.DeleteFile Fso.GetSpecialFolder(0)&"systemsvchost.exe"
'msgbox "U盘病毒完毕!欢迎访问我的百度空间:"&vbCrlf&vbCrlf&http://hi.baidu.com/MsRightHomepage,vbInformation+vbYesOnly,"MsRightHomepage 的“暴风一号”专杀工具 ~"
你也可以去www.84840.com的杀毒版块找答案。
 爱华网
爱华网