实践闯未来!本人FJXSUNMIT,初来报道,互相学习研究CISCO技术!
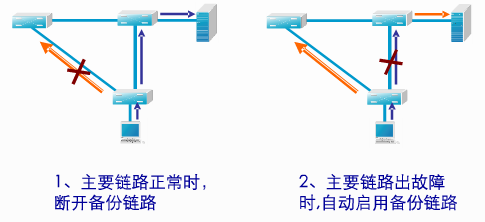
IPSec VPN设备链路冗余实验:(上为拓扑图)
基本实验配置:
R1:
R1#sh run
hostname R1
no ip domain lookup
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key sbb address 202.100.1.1
crypto isakmp key sbb address 61.128.128.1
crypto isakmp keepalive 10
!
crypto ipsec transform-set sbb esp-3des esp-md5-hmac
!
crypto map sbb 10 ipsec-isakmp
set peer 202.100.1.1
set peer 61.128.128.1【设置双peer】
set transform-set sbb
match address 100
!
interface Loopback0
ip address1.1.1.1 255.255.255.0
!
interface FastEthernet0/0
ip address10.1.1.1 255.255.255.0
duplex half
crypto map sbb【接口绑定加密图】
!
ip route0.0.0.0 0.0.0.0 FastEthernet0/0【指定静态路由】
access-list 100 permit ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255【匹配VPN流量】
!line con 0
exec-timeout 0 0
R1#
R2:
hostname R2
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key sbb address0.0.0.0 0.0.0.0
crypto isakmp keepalive 10【Keepalive时间】
!
crypto ipsec transform-set sbb esp-3des esp-md5-hmac【加密方式】
!
crypto dynamic-map sbb 10
set transform-set sbb
reverse-route【RRI动态反向注入更细化静态路由,使数据那里进,那里出!】
!
crypto map sbb 10 ipsec-isakmp dynamic sbb
!
interface FastEthernet0/0
ip address 202.100.1.1 255.255.255.0
duplex half
crypto map sbb【接口绑定加密图】
!
router ospf 1
log-adjacency-changes
redistribute static subnets
network2.2.2.0 0.0.0.255 area 0
default-information originate
!
ip route0.0.0.0 0.0.0.0 FastEthernet0/0
line con 0
exec-timeout 0 0
R3:
hostname R3
crypto isakmp policy 10
authentication pre-share
crypto isakmp key sbb address0.0.0.0 0.0.0.0
crypto isakmp keepalive 10
!
crypto ipsec transform-set sbb esp-3des esp-md5-hmac
!
crypto dynamic-map sbb 10
set transform-set sbb
reverse-route
!
crypto map sbb 10 ipsec-isakmp dynamic sbb
!
interface FastEthernet0/0
ip address 61.128.128.1 255.255.255.0
duplex half
crypto map sbb
!
interface Serial1/0
ip address2.2.2.3 255.255.255.0
serial restart-delay 0
!
router ospf 1
log-adjacency-changes
redistribute static subnets
network2.2.2.0 0.0.0.255 area 0
default-information originate
!
ip route0.0.0.0 0.0.0.0 FastEthernet0/0
line con 0
exec-timeout 0 0
R1#sh crypto isakmp sa
dstsrcstateconn-id slot
61.128.128.110.1.1.1QM_IDLE40
R1#sh crypto engine connections active
ID InterfaceIP-AddressStateAlgorithmEncryptDecrypt
4 FastEthernet0/010.1.1.1setHMAC_SHA+DES_56_CB00
2000 FastEthernet0/010.1.1.1setHMAC_MD5+3DES_56_C0251
2001 FastEthernet0/010.1.1.1setHMAC_MD5+3DES_56_C2510
R1#sh crypto ipsec sa
interface: FastEthernet0/0
Crypto map tag: sbb, local addr.10.1.1.1
protected vrf:
localident (addr/mask/prot/port): (1.1.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (2.2.2.0/255.255.255.0/0/0)
current_peer: 61.128.128.1:500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 1308, #pkts encrypt: 1308, #pkts digest 1308
#pkts decaps: 1268, #pkts decrypt: 1268, #pkts verify 1268
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 16, #recv errors 0
local crypto endpt.:10.1.1.1, remote crypto endpt.: 202.100.1.1
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
local crypto endpt.:10.1.1.1, remote crypto endpt.: 61.128.128.1
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: E6FFCD15
inbound esp sas:
spi: 0x93B5E8F5(2478172405)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 2000, flow_id: 1, crypto map: sbb
sa timing: remaining key lifetime (k/sec): (4425511/3307)
IV size: 8 bytes
replay detection support: Y
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xE6FFCD15(3875523861)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 2001, flow_id: 2, crypto map: sbb
sa timing: remaining key lifetime (k/sec): (4425511/3307)
IV size: 8 bytes
replay detection support: Y
outbound ah sas:
outbound pcp sas:
R1#sh crypto isakmp policy
Global IKE policy
Protection suite of priority 10
encryption algorithm:DES - Data Encryption Standard (56 bit keys).
hash algorithm:Secure Hash Standard
authentication method:Pre-Shared Key
Diffie-Hellman group:#1 (768 bit)
lifetime:86400 seconds, no volume limit
Default protection suite
encryption algorithm:DES - Data Encryption Standard (56 bit keys).
hash algorithm:Secure Hash Standard
authentication method:Rivest-Shamir-Adleman Signature
Diffie-Hellman group:#1 (768 bit)
lifetime:86400 seconds, no volume limit
R1#
实验测试结果:
R1#ping2.2.2.3 source 1.1.1.1 repeat 500
Type escape sequence to abort.
Sending 500, 100-byte ICMP Echos to2.2.2.3, timeout is 2 seconds:
Packet sent with a source address of1.1.1.1
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!.............!!!!!!!!!!!!【shutdown总部一接口时】
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!...
Success rate is 96 percent (484/500), round-trip min/avg/max = 44/107/1336 ms
R1#ping2.2.2.3 source 1.1.1.1 repeat 500
Type escape sequence to abort.
Sending 500, 100-byte ICMP Echos to2.2.2.3, timeout is 2 seconds:
Packet sent with a source address of1.1.1.1
..............!!
*Mar 15 14:36:51.599: %CRYPTO-4-IKMP_NO_SA: IKE message from 202.100.1.1has no SA and is not an initialization offer!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!.【顺利切换】
*Mar 15 14:37:10.283: %CRYPTO-4-RECVD_PKT_INV_SPI: decaps: rec'd IPSEC packet has invalid spi for
destaddr=10.1.1.1, prot=50, spi=0xF44B9632(-196372942), srcaddr=61.128.128.1.......!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
 爱华网
爱华网