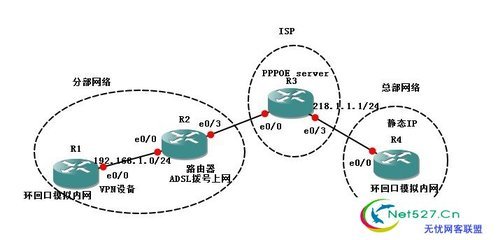
配置需求:总部是静态ip地址,分部是ADSL拨号的动态ip,而且vpn设备在adsl拨号设备后面,问两端如何做ipsecvpn。
配置过程:
1、配置ISP,R3做为PPPOEserver,主要命令如下
vpdn enablevpdn-group 1
accept-dialin
protocol pppoe
virtual-template 1
username cisco password cisco
ip local pool cisco 218.2.2.2 218.2.2.10
int lo0
ip add 218.2.2.1 255.255.255.0
int virtual-template 1
ip unnumber lo0
peer default ip address pool cisco
ppp authentication chap
int fa0/0
pppoe enable
no shut
int fa1/0
ip address 218.1.1.1 255.255.255.0
no shut
2、配置R2做为pppoe接入,主要命令如下
vpdn enablevpdn-group 1
request-dialin
protocol pppoe
interface Loopback0
ip address 10.1.1.1 255.255.255.0
!
interface FastEthernet0/0
no ip address
duplex auto
speed auto
pppoe enable group global
pppoe-client dial-pool-number 1
!
int dialer0
encapsulation ppp
ip address negotiated
ppp authentication chap pap callin
dialer pool 1
dialer-group 1
ppp chap hostname cisco
ppp chap password cisco
dialer-list 1 protocol ip permit
ip route 0.0.0.0 0.0.0.0 dialer 0
配置完成之后R2能看到获取的地址
R2#sh ipint bInterfaceIP-AddressOK? MethodStatusProtocol
FastEthernet0/0unassignedYES unsetupup
Virtual-Access1unassignedYES unsetupup
Virtual-Access2unassignedYES unsetupup
Dialer0218.2.2.2YES IPCPupup
Loopback010.1.1.1YES manualupup
配置R4的接入
interface Loopback0
ip address 10.100.1.1 255.255.255.0
!
interface FastEthernet1/0
ip address 218.1.1.2 255.255.255.0
duplex auto
speed auto
!
ip route 0.0.0.0 0.0.0.0 218.1.1.1
3、配置R2-R44台路由器的接口和NAT等,保证网络连通
R1#ping 218.1.1.2Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 218.1.1.2, timeout is 2seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max =24/52/108 ms
4、配置VPN
R2做VPN!
crypto isakmp policy 10
encr 3des
authentication pre-share
!
crypto isakmp key 0 cisco address 218.1.1.2
!
crypto ipsec transform-set cisco111 esp-3des esp-sha-hmac
!
crypto map vpnmap 1 ipsec-isakmp
set peer 218.1.1.2
set transform-set cisco111
match address 110
!
interface Loopback0
ip address 10.1.1.1 255.255.255.0
!
interface Dialer0
crypto map vpnmap
!
access-list 110 permit ip 10.1.1.0 0.0.0.255 10.100.1.00.0.0.255
R4端配置Dynamic-map
crypto isakmp policy 10
encr 3des
authentication pre-share
!
crypto isakmp key cisco address 0.0.0.0
!
crypto ipsec transform-set huawei esp-3des esp-sha-hmac
!
crypto dynamic-map huawei 1
set transform-set huawei
match address 110
!
crypto map vpnmap 1 ipsec-isakmp dynamic huawei
!
interface Loopback0
ip address 10.100.1.1 255.255.255.0
!
interface FastEthernet1/0
ip address 218.1.1.2 255.255.255.0
duplex auto
speed auto
crypto map vpnmap
!
access-list 110 permit ip 10.100.1.0 0.0.0.255 10.1.1.00.0.0.255
R4亦可做如下配置
crypto keyring k1
pre-shared-key address 0.0.0.0 0.0.0.0 keycisco
!
crypto isakmp policy 10
encr 3des
authentication pre-share
crypto isakmp profile l2l
keyring k1
match identity address0.0.0.0
!
!
crypto ipsec transform-set huawei esp-3des esp-sha-hmac
!
!
crypto dynamic-map vpnmap 1
set transform-set huawei
set isakmp-profile l2l
!
!
!
crypto map vpnmap 1 ipsec-isakmp dynamic vpnmap
配置完成之后在R2端发起感兴趣流(R4为动态map,所以只能由R2发起)
R2#ping 10.100.1.1 source loopback 0Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.100.1.1, timeout is 2seconds:
Packet sent with a source address of 10.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max =8/68/188 ms
最后查看一下R1和R4端的VPN状态
R2#sh crypto isakmp sadstsrcstateconn-id slot status
218.1.1.2218.2.2.2QM_IDLE1 0ACTIVE
 爱华网
爱华网